1、AFL下载和安装
1 | wget http://lcamtuf.coredump.cx/afl/releases/afl-latest.tgz |
安装好后,修改.bashrc加入环境变量export PATH=/usr/home:$PATH后即可使用。PATH为AFL的目录。
2、AFL Fuzzing步骤
1、使用afl-gcc编译项目代码,将编译脚本中的CC=afl-gcc/CXX=afl-g++;
2、新建两个文件夹,如fuzz_in/fuzz_out,文件夹名随意;
3、将初始化testcase放到fuzz_in目录下;
4、执行afl-fuzz -i fuzz_in -o fuzz_out ./xxx @@ xxx为可执行程序名,@@表示从文件中读入
5、观察fuzzing结果,如有crash,定位问题。
3、示例代码
1 | #include <stdio.h> |
1、有源码AFL测试
编译代码:
1 | afl-gcc afl.c -o afl_test |
准备环境
新建输入、输出文件夹:
1 | mkdir fuzz_in fuzz_out |
准备初始化testcase, 将testcase内容随意写成aaa:
1 | echo aaa > fuzz_in/testcase |
开始Fuzzing
1 | afl-fuzz -i fuzz_in -o fuzz_out ./afl_test @@ |
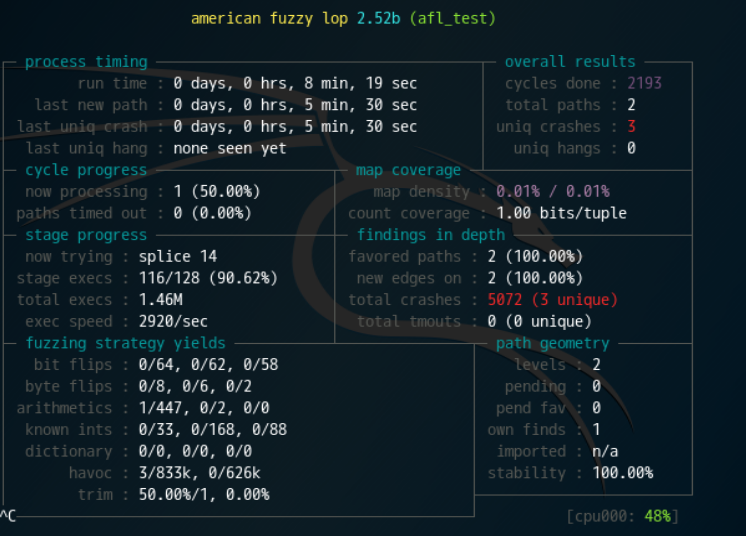
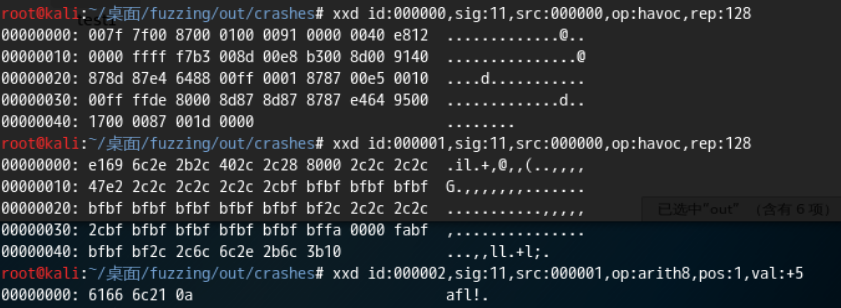
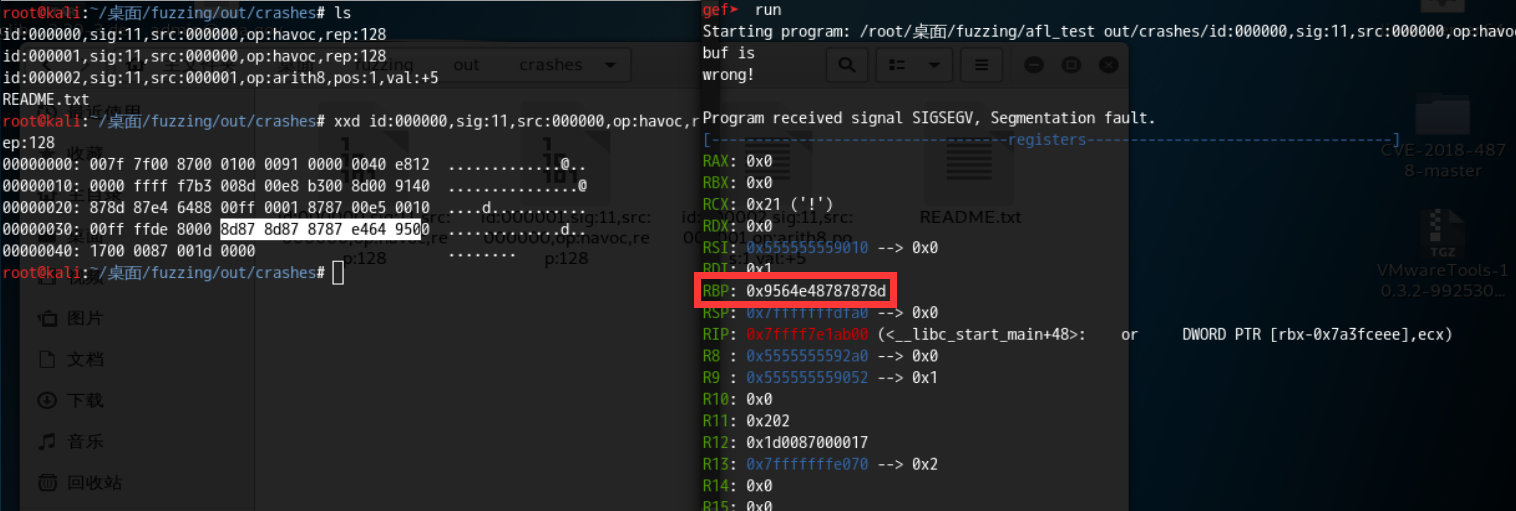
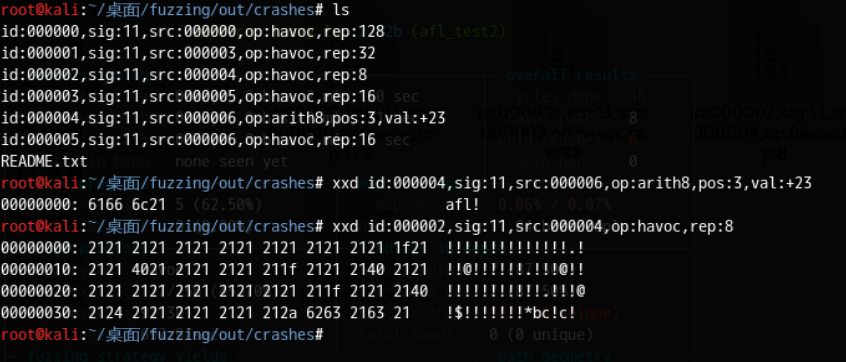
我们可以在fuzz_out/crashes中看到得到了三个crash。
2、无源码AFL测试
上面是对进简单的有源码的程序进行测试的,但是实际情况下不可能每次都有源码进行插桩编译测试,afl使用了qemu模式进行测试,只要在之前的命令的基础上加上-Q的参数即可,但是要先进行安装,在afl的根目录打开终端执行以下命令。
1 | cd qemu_mode |
在执行./build_qemu_support.sh命令时有两个报错
1 | static declaration of ‘memfd_create’ follows non-static declaration |
解决方法:
在patches目录下,将syscall.diff文件内容改成:
1 | --- qemu-2.10.0-clean/linux-user/syscall.c 2020-03-12 18:47:47.898592169 +0100 |
创建memfd_create.diff文件,写入:
1 | diff -ru qemu-2.10.0-clean/util/memfd.c qemu-2.10.0/util/memfd.c |
最后在加上build_qemu_support.sh文件中加上
1 | patch -p1 <../patches/memfd_create.diff || exit 1 |
完成之后再执行
1 | ./build_qemu_support.sh |
然后用gcc对测试文件进行编译
1 | gcc -g -o afl_test2 afl.c |
执行命令:
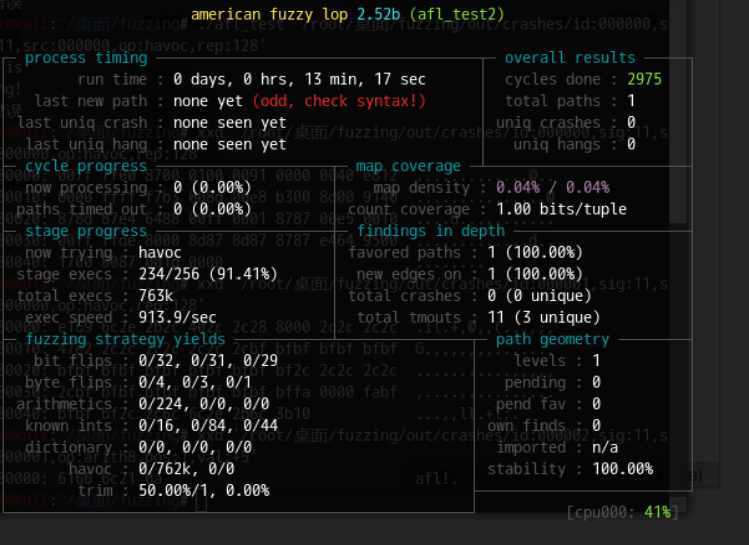
1 | afl-fuzz -i fuzz_in -o fuzz_out -Q ./afl_test2 @@ |